Blog
Recent Posts
Embedded CAN Bus Development with the ESP32 Processor
Posted by on
 The Controller Area Network (CAN) bus is a robust communication protocol designed to facilitate data exchange between microcontrollers and devices in automotive and industrial applications. With its high reliability and real-time capabilities, it has become a cornerstone in modern embedded systems. The ESP32, a popular microcontroller from Espressif Systems, offers integrated CAN controller support, making it a compelling choice for implementing CAN bus systems. This essay explores the development process of a CAN bus using the ESP32 processor.
The Controller Area Network (CAN) bus is a robust communication protocol designed to facilitate data exchange between microcontrollers and devices in automotive and industrial applications. With its high reliability and real-time capabilities, it has become a cornerstone in modern embedded systems. The ESP32, a popular microcontroller from Espressif Systems, offers integrated CAN controller support, making it a compelling choice for implementing CAN bus systems. This essay explores the development process of a CAN bus using the ESP32 processor.
Overview of CAN Bus
The CAN protocol, standardized as ISO 11898, was developed to address the need for reliable communication in noisy environments, particularly in automotive systems. It employs a multi-master, message-oriented architecture and uses differential signaling to reduce susceptibility to noise. CAN is highly efficient, capable of handling data rates up to 1 Mbps (Classical CAN) and beyond with the advent of CAN FD (Flexible Data Rate).
Why ESP32 for CAN Bus Development?
The ESP32 is a versatile microcontroller featuring dual-core processing, Wi-Fi, and Bluetooth capabilities. One of its lesser-known features is the integrated SJA1000-compatible CAN controller. When paired with an external CAN transceiver, such as the MCP2551 or TJA1050, the ESP32 can interface seamlessly with CAN networks. The combination of processing power, connectivity options, and cost-effectiveness makes the ESP32 ideal for developing modern CAN-based applications.
Steps for Developing a CAN Bus System with ESP32
- Hardware Setup:
- ESP32 Board: Select an ESP32 development board, such as ESP32 DevKit or NodeMCU.
- CAN Transceiver: Use an external CAN transceiver module to convert the ESP32’s logic-level signals to differential signals required by the CAN bus.
- Connections: Connect the ESP32's CAN controller pins (RX and TX) to the transceiver. Ensure proper termination resistors (typically 120 Ω) are in place on the CAN bus to maintain signal integrity.
- Software Configuration:
- Install the ESP-IDF (Espressif IoT Development Framework) or Arduino IDE with the necessary libraries for CAN communication.
- Use libraries like
ESP32CANor the native CAN driver provided in ESP-IDF.
- Programming:
- Initialize the CAN controller with appropriate baud rates, filters, and operating modes (e.g., Normal, Listen-Only, or Loopback).
- Write functions to send and receive CAN messages. Each message consists of an identifier, data length code (DLC), and data payload.
- Testing and Debugging:
- Use a CAN analyzer tool to monitor the bus and validate communication.
- Debug issues by checking electrical connections, analyzing timing errors, and verifying message configurations.
- Integration with Applications:
- Implement logic to process received messages and trigger actions based on application requirements.
- Use the ESP32’s connectivity features to bridge CAN data with other networks (e.g., Wi-Fi or Bluetooth).
Example Application: Vehicle Diagnostics
One practical application of the ESP32 with CAN bus is On-Board Diagnostics (OBD-II) for vehicles. By connecting the ESP32 to a vehicle’s CAN network via the OBD-II port, users can monitor engine parameters, read diagnostic trouble codes (DTCs), and send commands to the Electronic Control Unit (ECU). Additionally, the ESP32 can transmit this data over Wi-Fi to a smartphone app, providing a user-friendly interface for vehicle diagnostics.
Challenges and Solutions
- Noise and Interference: Use proper shielding and grounding to minimize electrical noise.
- Synchronization Issues: Ensure accurate timing configurations for the CAN controller to avoid synchronization errors.
- Compatibility: Verify compatibility between the ESP32, transceiver, and the existing CAN network.
Future Prospects
With the increasing adoption of CAN FD and Ethernet-based communication in modern vehicles and industries, the role of flexible microcontrollers like the ESP32 will expand. Integration of advanced features such as over-the-air updates and IoT connectivity can transform traditional CAN applications into intelligent systems.
Conclusion
The development of a CAN bus system using the ESP32 processor combines the reliability of the CAN protocol with the versatility of a modern microcontroller. Whether for automotive diagnostics, industrial automation, or IoT applications, the ESP32 provides a cost-effective and scalable solution. By leveraging its features and following best practices in hardware and software design, developers can create innovative and robust systems to meet the demands of a connected world.
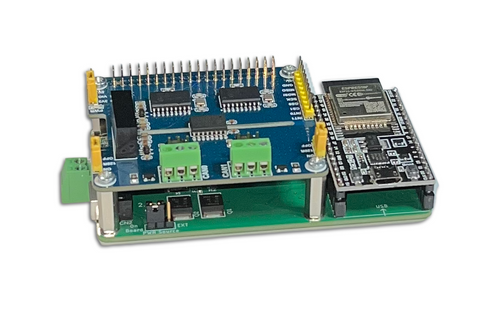 ESP32 Development Board with Dual Isolated CAN Bus HAT
ESP32 Development Board with Dual Isolated CAN Bus HAT
The espBerry DevBoard combines the ESP32-DevKitC development board with any Raspberry Pi HAT by connecting to the onboard RPi-compatible 40-pin GPIO header. The espBerry should not be viewed as an alternative to the Raspberry Pi but as a means of extending the ESP32’s functionality by tapping into the extensive range of RPi HATs available on the market and leveraging the many flexible hardware options.
The espBerry is an ideal solution for Internet of Things (IoT) applications, particularly those that require wireless capabilities. All open-source code samples utilize the popular Arduino IDE, which offers excellent programming features. More Information...
ESP32 Processor: Internal SJA 100 CAN Bus Controller
This post is an excerpt from our application note Controller Area Network (CAN) Development with ESP32.The ESP32 integrates a CAN Bus controller compatible with the NXP SJA1000. Thus, it is CAN 2.0B (ISO 11898, a.k.a. Classical CAN) specification-compliant.As with the SJA1000, the ESP32 CAN Bus controller provides only the data link layer and the physical layer [...]
The Myth: Controller Area Network is “Too Easy to Hack”
The potential security issues of CAN and its higher-layer protocols attract increased attention from the automotive, control, and medical industries. At first glance, believing that a well-documented standard like ISO 11898 makes it easier to manipulate control functions, whether in an automobile or a medical device such as an MRI or CT scanner, makes sense. [...]
Automotive Ethernet to CAN Bus Converter For Mobile SAE J1939, ISOBUS Applications
Axiomatic Technologies introduced their AX141530, a CAN-to-Ethernet protocol converter to support automation for mobile applications.The module translates CAN Bus 29-bit extended data frame to Automotive Ethernet (100 Mbit/s) and vice versa. It comes with Power, Link, and Speed LED indicators and an IP67 rating, making the product fitting for harsh environments, such as vibration and water resistance. [...]
Higher-Layer Protocol Specifications for CAN XL
The new year will see the release of CAN XL and its implementation into new applications. Additionally, CAN in Automation (CiA) will provide higher-layer protocol (HLP) specifications for CAN XL.Since its introduction, CAN XL, the third generation CAN protocol, was developed to interact with TCP/IP networks. The CAN XL protocol provides a layer management service access point [...]
Low-Cost CAN Bus Monitor For Developing And Debugging High-Speed CAN Networks
Controller Area Network (CAN) is a serial network technology that was originally designed for the automotive industry, especially for European cars, but has also become a popular bus in industrial automation as well as other applications. The CAN Bus is primarily used in embedded systems, and as its name implies, is a network technology that provides [...]
Controller Area Network (CAN Bus) Tutorial - Higher Layer Protocols
The following is an excerpt from A Comprehensible Controller Area Network by Wilfried Voss. Even though highly influential in automobiles and small applications, the CAN Bus technology alone is not suitable for machine automation since its communication between devices is limited to only 8 bytes. Consequently, higher layer protocols such as CANopen for machine control, DeviceNet for factory [...]
Controller Area Network (CAN Bus) Tutorial - CAN Bus Controller Firmware
The following is an excerpt from A Comprehensible Controller Area Network by Wilfried Voss. As demonstrated in the image below, the ISO/OSI Reference Model specifies seven levels beginning with the physical connection to the actual user application, i.e., the Application Layer. The standard CAN implementation bypasses the connection between the Data Link Layer and the Application Layer to [...]
Controller Area Network (CAN Bus) Tutorial - Remote Frame
The following is an excerpt from A Comprehensible Controller Area Network by Wilfried Voss. A Remote Frame requests the transmission of a message by another node. The requested data frame, identified by a unique message ID, may be accepted by any number of nodes in the network according to the individual application needs but can only be [...]
Controller Area Network (CAN Bus) Tutorial - Dominant And Recessive Bus Level
The following is an excerpt from A Comprehensible Controller Area Network by Wilfried Voss. Before discussing each bit in a CAN Bus frame, it is helpful to briefly examine the physical layer (for more details, refer to Chapter 9—Physical Layer) to understand the nature of, for instance, the SOF (Start of Frame) bit, the RTR (Remote Transmission [...]
 Loading... Please wait...
Loading... Please wait...
