Blog
Recent Posts
Industrial Ethernet Guide - Ethernet, CSMA/CD, TCP/IP, and UDP
Posted by on

The following is part of A Comprehensible Guide to Industrial Ethernet by Wilfried Voss.
The following chapter explains, in brief, the functionality of Ethernet, CSMA/CD (Carrier-sense multiple access with collision detection), TCP/IP (Transmission Control Protocol / Internet Protocol), and UDP (User Datagram Protocol).
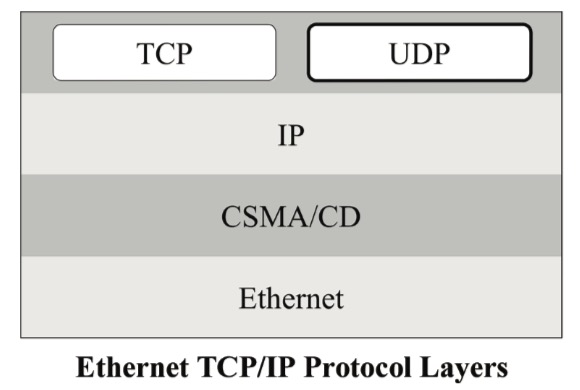
Ethernet
Ethernet represents the physical protocol layer, i.e., it covers the physical medium (e.g., cables, RJ45 ports, LAN cards, routers, switches, hubs, etc.) plus some basic, low-level protocol features.
Ethernet partitions a stream of data into individual packets called frames. Each frame contains source and destination addresses and error-checking data to ensure the detection of damaged data and initiate re-transmission when necessary.
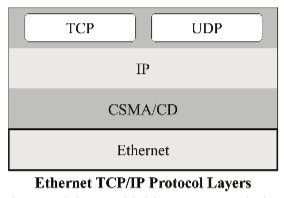
However, it is crucial to understand that most of the protocol control features are added by the layers above the Ethernet (physical) layer. Ethernet takes the data it receives, representing the application data plus several protocol control data, and transmits it into the network.
Too many references use the term “Ethernet” as a general term to describe the entire protocol, where it is essential to give credit where credit is due, and that is to the higher layers such as IP and TCP.
CSMA/CD
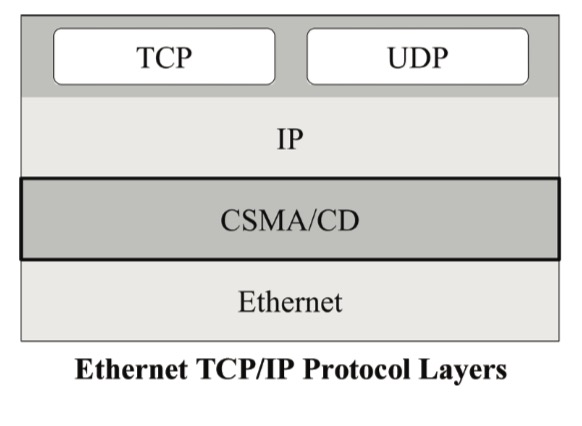
In basic terms, CSMA/CD describes the bus arbitration process, i.e., the process that assures proper data exchange and prevents data damage or loss.
The acronym CSMA/CD stands for “carrier-sense multiple access with collision detection,” and it describes how Ethernet regulates the communication between nodes (devices) in a network. To understand this (almost intimidating) term, it is helpful to look at the individual components.
The portion “multiple access” covers the procedure of a “polite” conversation, meaning it is a proper protocol that one party speaks (transmits data) while all other participants listen (receive data).
Using the same scenario of a polite conversation, it would be an improper protocol to interrupt the speaker (transmitter) and thus damage or even lose the message. “Carrier sense” describes the process of “listening” to the conversation (the physical medium) to determine if another party is still speaking (transmitting). When the medium is quiet (i.e., the conversation ceased), it is the appropriate time for another station to transmit data.
While CSMA is an excellent start to regulate the data communication process, however, it does not cover the scenario of message collision. A message collision can occur when two stations attempt to transmit data at the same time.
“Collision detection” assures that Ethernet nodes listen to the medium while they transmit. If several transmitting nodes detect their transmission in a distorted form, they assume that a collision occurred, in which case they will cease the transmission, destroy their frame, and wait a random amount of time before they attempt to transmit again.
However, the new transmission attempt is preceded by a “carrier sense,” which will determine whether bus access is possible. The random delay between ceasing the transmission and carrier sense makes it unlikely that node transmissions will collide more than a few times in a row.
There is, however, a significant downside to CSMA/CD: As the number of nodes in a network grows and, consequently, the volume of traffic increases, opportunities to gain access to the network decrease.
The number of collisions will increase exponentially, and the probability of getting access within a given length of time decreases dramatically. In the worst-case scenario, when message collisions occur continuously, nodes will dump the message frame and will not attempt a re-transmission.
TCP/IP
In review, TCP/IP stands for Transmission Control Protocol / Internet Protocol, and it is a layered protocol where TCP/IP works on top of Ethernet including its CSMA/CD component.
TCP and IP are two distinct protocols, but they are commonly used in a combined way that has become the standard terminology referring to either or both protocols.
IP corresponds to the Network Layer (Layer 3) in the OSI 7-Layer Model, whereas TCP corresponds to the Transport Layer (Layer 4) in OSI. In other words, the term TCP/IP refers to network communications where the TCP transport is used to deliver data across IP networks.
Internet Protocol IP
IP is the fundamental protocol of TCP/IP. Every piece of data sent per TCP/IP is sent as an IP packet
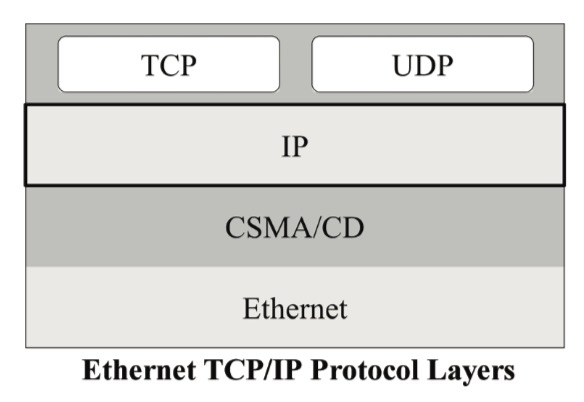
IP supports unique addressing for nodes in a network. Most networks use the Internet Protocol version 4 (IPv4) standard that features IP addresses four bytes (32 bits) in length.
The newer Internet Protocol version 6 (IPv6) standard features addresses of 16 bytes (128 bits) in length.
Data on an Internet Protocol network is organized into packets, and each IP packet includes both a header (specifying a source and destination address, and data characteristics) and the message data itself.
IP Features:
- IP is a connectionless protocol; it has no concept of a job or session, meaning each data packet is treated as entity in itself.
- IP is in so far an unreliable protocol as it is not concerned with whether a data packet reaches its destination, or whether they arrive in the original order. IP also cannot tell if packets were lost or received out of order.
While all these characteristics don’t appear attractive to establish a data connection, it is the higher-level TCP protocol that provides the reliability (and thus demonstrating the effectiveness of layered protocol suite).
A protocol field in the IP’s header information identifies which higher-level TCP/IP protocol sent the data. When IP receives data, this field tells which protocol module to pass it on.
Transmission Control Protocol TCP
The Transmission Control Protocol (TCP) accepts data from a data stream, divides it into chunks, and adds a TCP header, thus creating a TCP segment. The TCP segment is then encapsulated into an Internet Protocol (IP) datagram and exchanged with peers.
In other words, TCP’s primary use is to establish communication between applications.
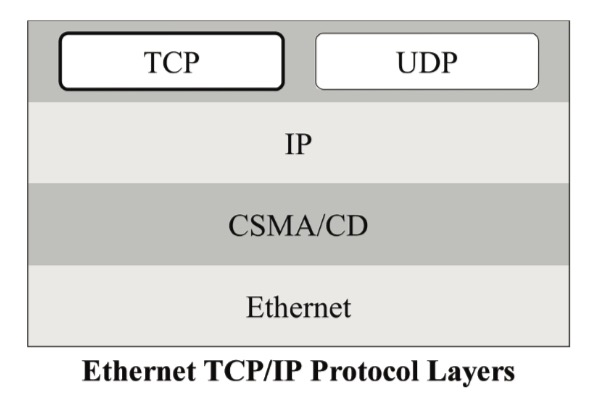
An application that needs to initiate a communication with another via TCP sends a communication request, which must be sent to an exact address.
After a “handshake” between the applications, TCP will set up a “full-duplex” communication between the two applications, which will remain open until it is closed by either one of the applications.
TCP Features:
- TCP sends data (using IP) in segments, also using sequence numbers to identify the position in the data stream.
- TCP is a connection-oriented protocol, meaning client and server must establish a connection before any data can be transferred.
- TCP knows that transmitted data was received, and that it was received correctly. It ensures that received data is put into order even when it arrives out of order.
- TCP also implements flow control (message acknowledgement) to prevent a message overflow.
- TCP uses checksums to assure correct data.
UDP - User Datagram Protocol
UDP (User Datagram Protocol) is a simple communications protocol that offers a limited amount of service. It is an alternative to the Transmission Control Protocol (TCP) and, together with IP, is sometimes referred to as UDP/IP.
Like the Transmission Control Protocol, UDP uses the Internet Protocol (IP) to transmit a data unit from one network node to another.
Unlike TCP, UDP does not provide the service of dividing a message into segments and reassembling it at the other end. Specifically, UDP does not provide sequencing of the data packets. Consequently, the application program that uses UDP must assure that the entire message has arrived and that is in the right order. Network applications that need to save processing time because they have small data units to exchange (and therefore minimal message reassembling to do) may prefer UDP to TCP.
TCP/IP Addressing: MAC and IP Address
MAC (Media Access Control) and IP (Internet Protocol) are the two addresses that identify a computer in a network. They are used to track data packages and ensuring they are transmitted and received correctly.
A Static IP Address is an address, usually assigned by the network administrator, which does not change over time unless changed manually. It is used when there is a need for the IP address or network location to remain the same consistently.
A Dynamic IP Address is temporarily assigned to a device, i.e. the address is leased from a DHCP (Dynamic Host Configuration Protocol) server for a period of time, and when the lease expires the computer will request a renewal or a new IP address.
TCP/IP (IPv4 Standard) uses 32 bits (four numbers between 0 and 255) to address a node (computer) in the network. IP addresses are normally documented as four numbers separated by a period in the form of, for instance, 192.168.1.50.
Each node must have an IP address before it can connect to the network, and that address must be unique. In other words, each IP packet must have the proper address information before it can be sent to another node.
A MAC Address, also known as hardware or physical address, is a unique value associated with the actual, physical network adapter.
MAC addresses are 12-digit hexadecimal numbers (48 bits in length), a format following the IEEE 802 standard. By convention, MAC addresses are usually documented in either one of the following formats:
MM:MM:MM:SS:SS:SS
MM-MM-MM-SS-SS-SS
The first half of a MAC address, represented by “MM,” contains the ID number of the adapter manufacturer. The second half of a MAC address, represented by “SS,” denotes the serial number assigned to the adapter by the manufacturer.
The IEEE is also the body that assigns manufacturers their IDs, called Organizationally Unique Identifiers, and the manufacturer assigns the second half, called the Universal LAN MAC address.
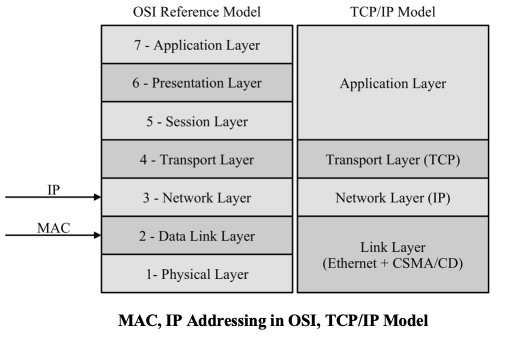
In reference to the OSI Reference Model, MAC addressing is located at the Data Link Layer (Layer 2), allowing computers to uniquely identify themselves at this comparatively low level, whereas IP addressing functions at the Network Layer (Layer 3).
There may be a risk of oversimplifying matters, but, in a mere educational view, IP addressing can be considered as supporting the software implementation, while MAC addressing supports the hardware implementation of the network stack.
TCP/IP Illustrated, Volume 1: The Protocols
TCP/IP Illustrated, Volume 1, Second Edition, is a detailed and visual guide to today’s TCP/IP protocol suite. Fully updated for the newest innovations, it demonstrates each protocol in action through realistic examples from modern Linux, Windows, and Mac OS environments. There’s no better way to discover why TCP/IP works as it does, how it reacts to standard conditions, and how to apply it in your applications and networks.
Building on the late W. Richard Stevens’ classic first edition, author Kevin R. Fall adds his cutting-edge experience as a leader in TCP/IP protocol research, updating the book to reflect the latest protocols and best practices fully. He first introduces TCP/IP’s core goals and architectural concepts, showing how they can robustly connect diverse networks and support multiple services running concurrently. Next, he carefully explains Internet addressing in both IPv4 and IPv6 networks. Then, he walks through TCP/IP’s structure and function from the bottom up: from link layer protocols–such as Ethernet and Wi-Fi–through the network, transport, and application layers.
 Loading... Please wait...
Loading... Please wait...

