Recent Posts
CANopen Module For Raspberry Pi And Other Embedded Systems
Posted by on
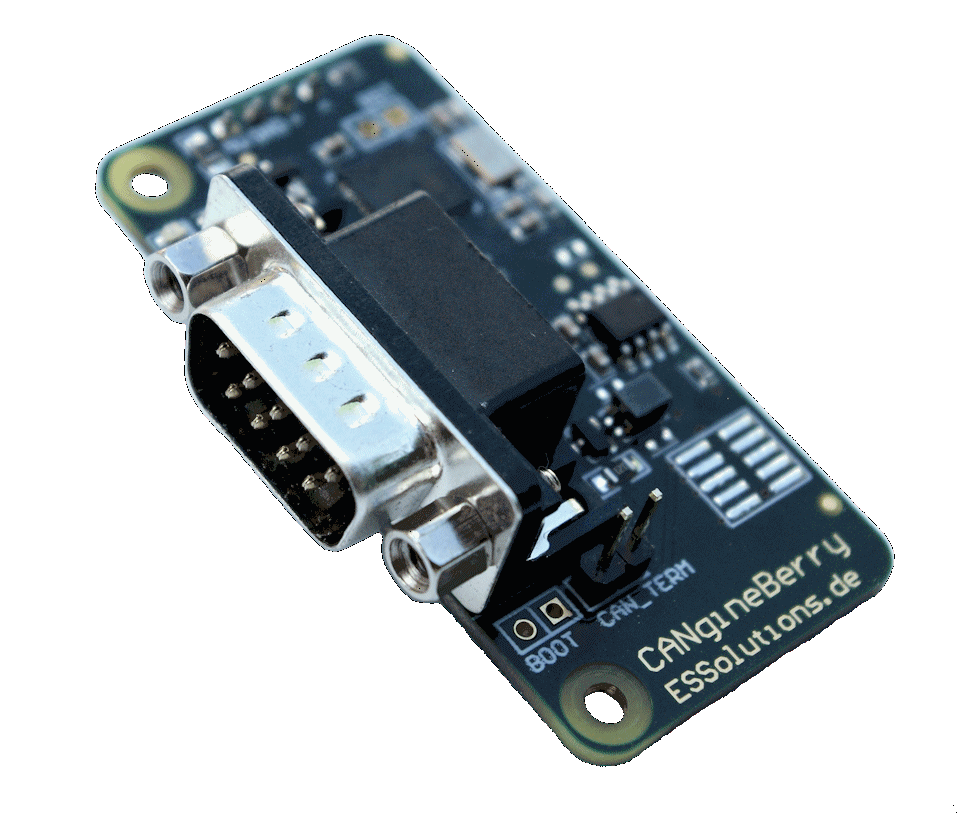 Emsa (formerly Embedded Systems Academy) announced their new product, the CANgine-Berry, an active CAN co-processor module that uses a regular UART communication channel towards the host system. With its independent 32-bit micro-controller, the product can execute CAN protocols with tough timing demands such as CANcrypt or CANopen with response times of under 10 ms. Depending on the configuration, the CAN communication can be up and running within 50 ms after power-on, even if the host system takes significantly longer to boot.
Emsa (formerly Embedded Systems Academy) announced their new product, the CANgine-Berry, an active CAN co-processor module that uses a regular UART communication channel towards the host system. With its independent 32-bit micro-controller, the product can execute CAN protocols with tough timing demands such as CANcrypt or CANopen with response times of under 10 ms. Depending on the configuration, the CAN communication can be up and running within 50 ms after power-on, even if the host system takes significantly longer to boot.
Available firmware options at launch include a generic minimal CANopen Manager/Controller and a CANopenIA Device both based on the CANopenIA implementation by the company. Within the next weeks, Emsa will also release a CANcrypt version of the Lawicel protocol (SLCAN).
The connection to the host system uses only four pins: Two for power (5 V) and two for the UART. The four-pin header row directly matches the Raspberry Pi pin layout, but also other common connectors. This includes USB-to-UART converter chips/modules, if the correct voltage levels are used (5 V supply, 3,3 V signals).
The serial protocol between host and CANopenIA is the CANopen remote access protocol by Embedded Systems Academy. It supports reporting events (new data arrived on CANopen side) as well as reading and writing data of the local Object Dictionary.
The CANopen Manager performs automatic network scans, simplifying application code as it can directly access the data scanned. CANopen Manager implementations also support read and write accesses to Object Dictionary entries of any node connected to the CANopen network.
When the Controller Area Network (CAN) was designed, security was not a requirement. The primary usage of CAN was considered closed; possible intruders or attackers would simply not get physical or remote access to the network.
However, today it is more and more common that devices connected to a CAN system also have connections to other networks, including the Internet. Recent car hacks have shown that attackers may get access to CAN systems. Without strong security features, an attacker automatically gains full access to everything connected, allowing active control commands to be recorded and replayed.
In this book we examine which options developers of CAN based systems realistically can use to provide adequate security features. What can we do - without using heavy-weight security features? What can we do - to detect possibly injected messages? What can we do - without any hardware change? What can we do - with minimal software change?
The CANcrypt protocol and software is introduced as a scalable security solution for the Controller Area Network. Free demo examples including C source code can be downloaded from ESAcademy's web pages.
 Loading... Please wait...
Loading... Please wait...

