Blog
Recent Posts
OBD2 Bluetooth Scanner for iPhone, Android, and Windows
Posted by on
 The OBDLink MX+ is a unique wireless OBD adapter that transforms any iPhone, iPad, or Android device into a professional-grade diagnostic scan tool, trip computer, and real-time performance monitor capable of accessing manufacturer-specific vehicle data.
The OBDLink MX+ is a unique wireless OBD adapter that transforms any iPhone, iPad, or Android device into a professional-grade diagnostic scan tool, trip computer, and real-time performance monitor capable of accessing manufacturer-specific vehicle data.
The newest addition to the OBDLink family is even faster, more reliable, and features richer than its predecessors.
It is the only wireless iOS-compatible scan tool on the market that supports the proprietary GM-LAN and Ford MS-CAN vehicle networks. This tool provides access to dozens of additional ECUs and thousands of manufacturer-specific trouble codes and parameters, including ABS, SRS, TPMS, A/C, transmission temperature, and wheel speeds.
While other solutions can display real-time data, the OBDLink MX+ is optimized for maximum throughput. It delivers up to four times more data samples per second than its closest competitor, which results in smoother gauges and graphs and allows the display of multiple parameters simultaneously.
OBDLink MX+ incorporates features not found in competing adapters that make it safe to leave plugged in, including hacker-proof wireless security, overvoltage/load dump protection, and ultra-low current sleep mode.
The MX+ offers complimentary firmware upgrades and free technical support for peace of mind.
Features
- Turn your iPhone, Android device, or Windows PC into a professional-grade diagnostic scan tool.
- This is the recommended adapter for FORScan, Torque, BimmerCode, Dashcommand, AlfaOBD, Carista, and many more.
- Enhanced OEM support for Ford, GM, Mazda, Nissan/Infinity, Toyota/Lexus/Scion, Honda, Hyundai, Kia.
- Clear Check Engine Light and get more live parameters (ABS, SRS, TPMS, etc) than any other scanner.
- Over-voltage and battery drain protection and firmware updates are included.
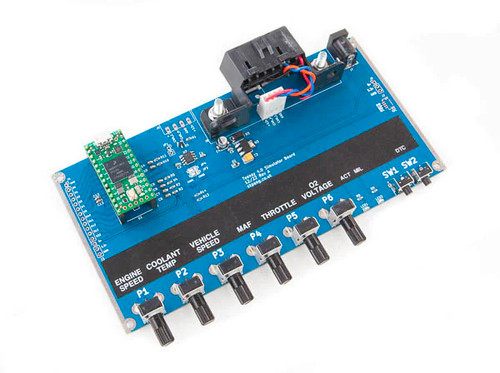 Teensy 4.0 OBDII CAN-Bus ECU Simulator
Teensy 4.0 OBDII CAN-Bus ECU Simulator
This is a CAN-Bus OBDII ECU simulator that uses the Teensy 4.0 module (which is included). It's designed to test the OBDII interface and write diagnostic software. The Teensy processor is included and pre-programmed with the OBDII ECU simulator firmware.
Potentiometers can be used to adjust the ECU PID parameters. This board requires a 12 VDC power supply, and a 12 VDC adapter is included. More Information...
OBD2 Bluetooth Scanner with App for iOS & Android
The V011 OBD2 Scanner provides a complete diagnostic solution, thoroughly understanding your vehicle's condition. It supports a variety of performance tests, including fast reading of DTCs, access to electronic emission readiness, turning off the CEL or MIL, resetting monitors, reading live data, retrieving the vehicle's VIN, checking battery health, accessing freeze frame data, reviewing sensor data, [...]
Diesel Diagnostic Scan Tool for J1587/J1708, J1939 Trucks
The KZYEE KC601 scanner module is the newest portable heavy-duty vehicle code reader. It can quickly and efficiently read DTCs in the truck's electrical control system, diagnose the fault location, and find the cause of the fault. It is beneficial for all auto repair shops to read and clear fault codes and read live data. The scanner [...]
SAE J1939 and OBD2 Heavy Duty Truck Scanner and Diagnostics
DPF Force Regen & Reset for Cummins Caterpillar Engine -- Reset and clean your DPF professionally, quickly, and efficiently to ensure your engine runs smoothly and meets emissions standards. This all-in-one solution saves you money on maintenance costs. The Inspection Record feature records all DPF inspections to help track and manage maintenance schedules. Full System Diesel [...]
OBD-II and the Hacking of Automotive CAN Bus Networks
Let me clarify: this is not a guide to hacking automotive networks. Instead, I attempt to dismiss some common misconceptions about OBD-II and its supposed ability to control a vehicle (Spoiler alert: It cannot). As someone who has spent considerable time studying and working with CAN Bus technologies, I think it is time to set [...]
Bluetooth OBD2 Scanner and Code Reader for iPhone & Android
EASY-TO-USE OBD2 APP & CAR CODE READER - The FIXD car scanner and OBD app instantly translates 7000+ engine fault codes into plain English on your phone. Wireless Bluetooth connection. Set up in minutes. No car knowledge needed. FIND OUT WHAT’S WRONG WITH YOUR CAR - Even beginners can use the FIXD OBD2 scanner and app [...]
Contactless CAN Bus, SAE J1939, OBD-II, SAE J1708 Reader
CAN (J1939) and J1708 networks transport multiple valuable information for telematics of vehicles and stationary objects, such as engine parameters, ABS, EPS, diagnostic codes (DTC), and much more. Crocodile contactless readers are used in telematics systems to gather data from digital buses without breaking the insulation of wires and electrical contacts and without sending active requests [...]
Free-of-Charge OBD-II Viewer Windows Software and Application Programming Interface (API)
PEAK Systems has announced the revised version 1.2 of its free-of-charge Windows software PCAN-OBD-2, an OBD-II Viewer based on their OBD-2-API (Application Programming Interface). The software allows engineers to develop applications based on the OBD-II (Onboard Diagnostics) communication standard. The Windows software and the API work with all PEAK Systems CAN Bus interfaces. OBD-II is a standard specifying [...]
4G Telematics Unit With OBD-II (CAN Bus) Port For Fleet Management
The TMU Pi3 telematics unit by Autopi (Denmark) utilizes the Raspberry Pi 3 Model A+ SBC, and it connects to in-vehicle CAN Bus networks via the OBD2 port.The device uses the 1,4-GHz Broadcom BCM2837B0 SOC with Cortex-A53 64-bit quad-core processor, including 512-MiB SDRAM and a 32-GiB micro SD card with installed Raspbian Jessie operating system and Autopi [...]
Contactless Monitoring Of CAN Bus, SAE J1939, FMS, OBD-II, And SAE J1708 Data Traffic
Copperhill Technologies offers the CANCrocodile product line of contactless CAN Bus monitoring devices for vehicle telematics, GPS tracking systems, and various CAN Bus data frames.The CANCrocodile product line was designed for secure and reliable data reading from any CAN Bus network. The contactless reader is specifically suitable for vehicle telematics, GPS tracking systems and for [...]
 Loading... Please wait...
Loading... Please wait...
